Secure. Open. Stackable.


Secure. Open. Stackable. The Resilient Data Platform
The Stackable Data Platform
Stackable's Commitment to Security
In today’s digital age, with prominent attacks like Log4Shell, the xz backdoor and the SolarWinds hack making headlines, the importance of the software supply chain has never been clearer.
At Stackable, as a provider of data platforms that process large volumes of potentially sensitive data, we recognize the critical role we play in this chain.
That’s why, especially at a time when regulations like the EU Cyber Resilience Act (CRA) and the US President’s Executive Order (EO) 14028 on Improving the Nation’s Cybersecurity are increasingly pushing companies to raise their security levels, we want to assure the Stackable community of our strong commitment to security.

Stackable’s security approach
Our supply chain security initiatives
At Stackable, we like to work with this general flow of accountability when it comes to modern supply chain security:
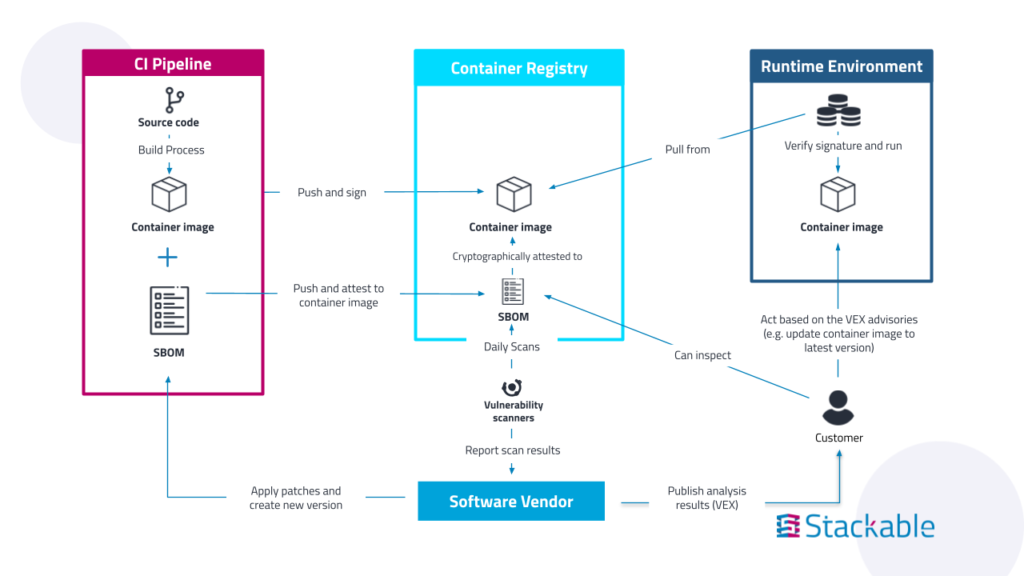
To that end, we are ensuring the security of our software supply chain through a number of measures:
- Publishing signed SBOMs (Software Bill of Materials): As all our code is fully open source, transparency of what components we use was always given anyway. With SBOMs, we make this information machine readable and much easier to access.
- Daily Vulnerability Scans: Our products undergo daily scans with multiple scanners to identify and address vulnerabilities promptly. Additionally, we are also subscribed to relevant mailing lists publishing security relevant information about the tools we use in our platform.
- Critical Vulnerability Analysis: We prioritize and thoroughly analyze critical vulnerabilities based on various metrics to mitigate risks effectively.
- Keyless Signing: All our container images and Helm Charts are signed using cosign within Github Actions, ensuring their integrity and authenticity.
- Securing Our CI on Github: We enforce Multi-Factor Authentication (MFA) and verified commits to protect our Continuous Integration (CI) processes.
Ensuring Data Security at Runtime
In addition to security in the software supply chain, the Stackable Data Platform also offers various security-related protection functions at runtime:
- Integration of Open Policy Agent: Our platform incorporates policy-based authorization to control access and operations.
- Kerberos, OIDC, LDAP and More: We support Kerberos, LDAP and OpenID Connect (OIDC) for secure and industry standard authentication mechanisms.
- Row and Column-Based Security: To comply with regulations like GDPR, we offer ways to implement row and column-based security and masking. This ensures that sensitive information, such as email addresses, is adequately protected and certain data is accessible only to authorized teams.
- Secure TLS Configuration: By default, our platform uses a secure TLS configuration to safeguard data in transit.
- Custom Resource Definitions (CRDs): CRDs allow you to customize the security status, making it easy and flexible to meet the specific security requirements of a data architecture. Since all this configuration is stored as code, it can be versioned, audited, linted and reviewed.
- Support for air gapped environments: Stackable Data Platform can be run in completely air gapped environments, eliminating the risk of attacks via or data leakage into the internet.
Looking Ahead
We believe that security is a continuous journey, not a destination. Our team is constantly working on further enhancing our security measures. Reproducible builds, transitive SBOMs, SLSA, TACOS, VEX and CSAF are some of the initiatives we are actively working on. We will continue to share information about our progress in these areas. Stay tuned for more updates on how we continue to further strengthen our security measures to for the protection of your data.
We support you...

Secure Data Platform Consulting
Our Professional Services team is ready to assist you with your unique security needs.
From initial secure platform design, to implementation assistance, to security assessments of existing installations, we offer a wide range of services for data platform security.
We want you to have the most secure Stackable experience possible without risking security breaches.
Security in Community Edition & beyond
Even our Community Edition already benefits from our Software Vulnerability Management. With proactive monitoring and detailed SBOMs, we are providing a clear view and control over potential vulnerabilities, ensuring a more secure and resilient data architecture at no extra cost.
Additionally, get access to our published Vulnerability Exploitability eXchange (VEX) information for open source data apps by subscribing to one of our commercial plans.
Glossary
VEX, Vulnerability Exploitability eXchange: A software vendor can publish information about vulnerabilities in its products in the form of VEX. The goal is to provide additional, context aware information to the publicly available general information provided by for example NVD. Users of the software can get product specific, security relevant information like possible threats, mitigations, false positives or available patches. VEX itself is not a specific format, but is distributed via formats like CSAF, OpenVEX or CycloneDX.
An SBOM (Software Bill of Materials) is a detailed inventory list that itemizes the components, libraries, and dependencies used in a software product or system. It provides transparency and visibility into the software supply chain, aiding in risk management, vulnerability detection, and compliance efforts. SBOMs are increasingly important for cybersecurity and ensuring the integrity and security of software throughout its lifecycle.
A Kubernetes CRD (Custom Resource Definition) extends the Kubernetes API to support custom resources, enabling users to define and manage their own resource types alongside native Kubernetes objects. In the case of Stackable, the Stackable Data Platform ships predefined CRDs to make it easy for users to achieve a certain configuration by specifying it on a high level via the CRD and letting the Stackable operators take care of all the details. Examples would be an Authentication Class or a Zookeeper Cluster.
CSAF (Common Security Advisory Framework) is a standardized format for documenting and sharing security advisories and vulnerability relevant information across the cybersecurity community. It provides a structured way to convey important information about security issues, including details such as affected software versions, severity ratings, and mitigation strategies.
SLSA (Supply-chain Levels for Software Artifacts) is a framework for assessing the security and integrity of software supply chains. It defines a set of maturity levels and requirements that organizations can adopt to enhance the trustworthiness of their software artifacts throughout the development and distribution process.
Let's get in contact!
How can we support you?
Contact Lars:

Lars Francke
CTO & Co-Founder of Stackable
Subscribe to our Newsletter


Newsletter
Subscribe to the newsletter
With the Stackable newsletter you’ll always be up to date when it comes to updates around Stackable!